In today’s rapidly evolving cyber threat landscape, information stealers — or “infostealers” — have become a pervasive and escalating threat. These stealthy malware variants are specifically engineered to harvest sensitive data from compromised systems, including credentials, financial information, and personal identifiers, and exfiltrate it to remote attackers for exploitation. Both individuals and organizations are increasingly in their crosshairs, making infostealers a critical concern in modern cybersecurity.
More than half of ransomware victims in recent incidents had their domains appear in stealer logs, revealing a strong correlation between infostealer infections and high-impact cyberattacks. This connection is further reinforced by a year-over-year surge in phishing campaigns delivering infostealers, enabling threat actors to scale credential theft with minimal effort. In 2024, tools like Lumma, RisePro, Vidar, Stealc, and RedLine dominated the cybercrime ecosystem, emerging as the five most advertised infostealers across Dark Web forums. These tools have become instrumental in initial access operations, often serving as precursors to ransomware deployment and other advanced intrusions.
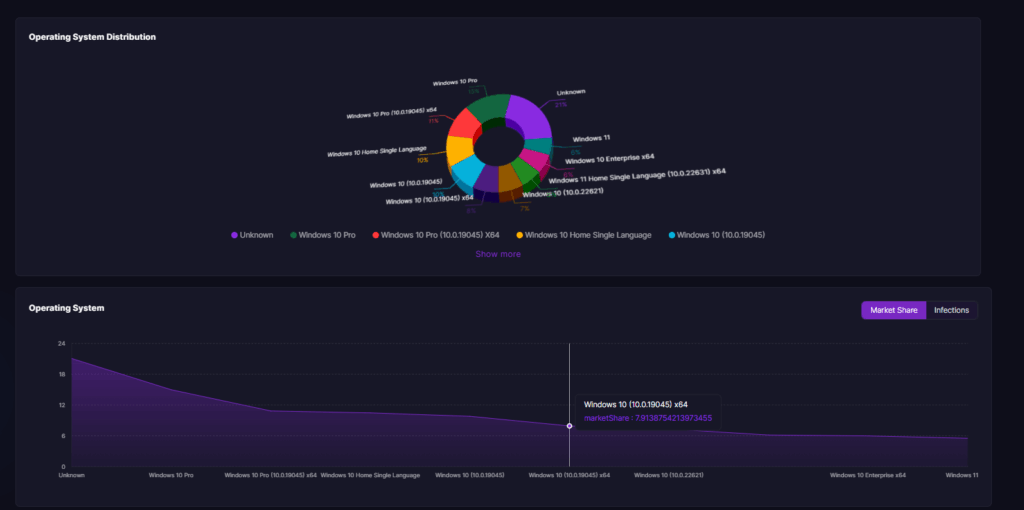
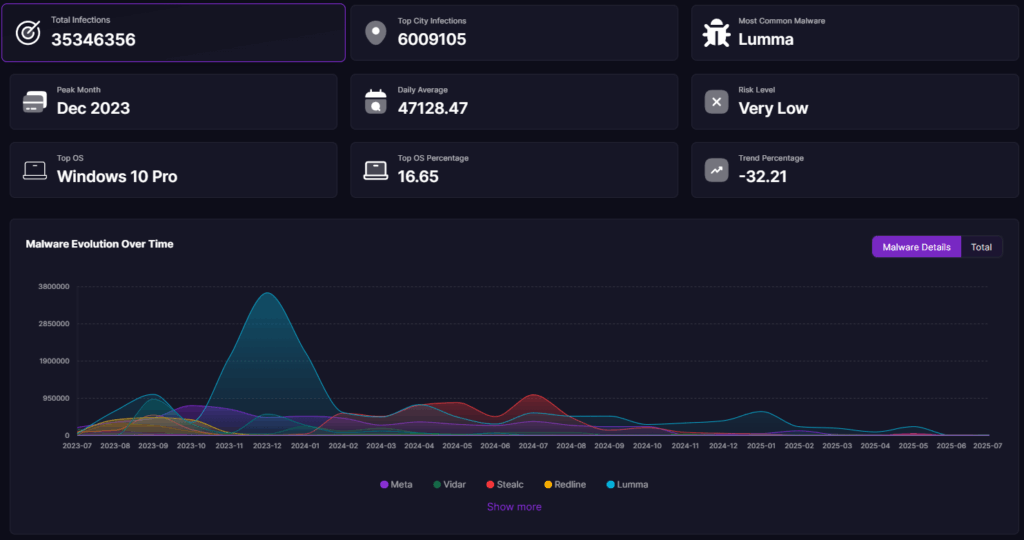
What Are Stealer Logs?
Stealer logs are structured collections of sensitive data extracted from compromised devices following an infostealer infection. Once a system is breached, infostealer malware silently gathers valuable information such as login credentials, browser cookies, cryptocurrency wallet details, system metadata, and more.
This stolen data is then compiled into easily accessible logs that cybercriminals can sort, search, and exploit for further attacks, including account takeovers, identity theft, and initial access for ransomware deployment.
Prolific Infostealer Families
Several malware families are known for their high volume of stealer log generation. Among the most prevalent are:
- RedLine
- Raccoon
- Vidar
These families play a critical role in fueling the underground economy by helping threat actors build massive repositories of stolen information, which are actively traded on Dark Web markets and cybercrime forums.
What Data Do Infostealers Target?
Infostealers are designed to extract a wide range of information from compromised systems, including but not limited to:
- Login Credentials: Usernames, email addresses, and passwords for websites and applications
- Financial Information: Credit card numbers, banking credentials, and online payment details
- Personal Data: Social Security numbers, home addresses, phone numbers, and other PII
- Browser Data: Saved passwords, cookies, bookmarks, and browsing history
- Emails and Chat Logs: Extracted from mail clients and messaging applications
- Files and Documents: Including sensitive images, business documents, and PDFs
- Cryptocurrency Wallets: Desktop wallet files and browser extension data
- Screenshots: Some variants periodically capture screen activity and send it to attackers
How Do Infostealers Work?
Infostealers are frequently deployed alongside other malware families to facilitate broader intrusion campaigns — including ransomware, banking trojans, and remote access tools. They are typically delivered via phishing emails, malicious websites, drive-by downloads, or trojanized software.
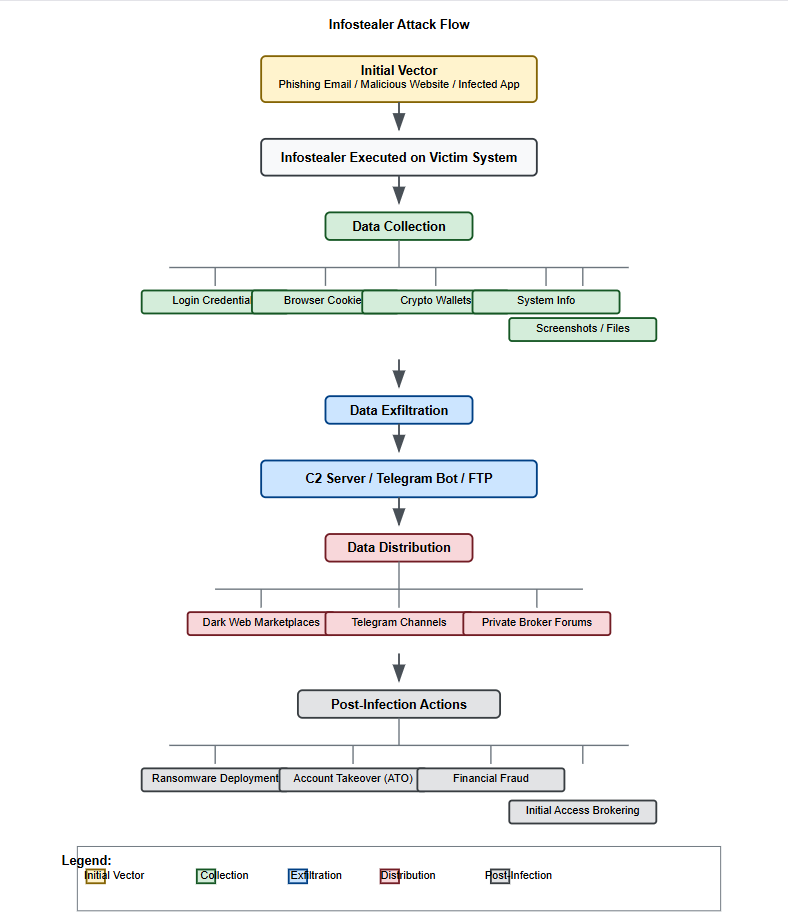
Their operation can be broken down into five main stages:
1. Infostealer Delivery
The attack begins when the user interacts with a malicious payload — typically through:
- Phishing emails with weaponized attachments or links
- Drive-by downloads from compromised websites
- Cracked/pirated software or fake installers
2. Data Collection
Once executed, the infostealer silently:
- Harvests saved credentials, cookies, autofill data
- Extracts crypto wallet files
- Scans for files, documents, chat logs, and screenshots
3. Data Exfiltration
The stolen data is:
- Packaged into structured logs (e.g., JSON or ZIP)
- Exfiltrated to attacker-controlled servers via HTTP/S, FTP, or Telegram bots
4. Data Distribution
The logs are then:
- Sold or traded on dark web markets or Telegram channels
- Indexed in searchable stealer log databases
5. Further Criminal Activity
Attackers use the stolen data for:
- Credential stuffing, identity theft, financial fraud
- Initial access for ransomware or APT campaigns
- Bypassing MFA or hijacking sessions
Data Collection Tactics Used by Infostealers
Once installed on a victim’s machine, infostealers initiate a covert data-gathering process, employing a range of techniques to extract valuable information. These methods target both user activity and system-stored assets, making infostealers particularly effective and dangerous. Below are the core techniques used:
1. Keylogging
Nearly all infostealers embed a keylogger component that records every keystroke typed by the user. This allows attackers to reconstruct:
- Usernames and passwords
- Credit card information
- Private messages
- Typed commands and notes
2. Form Interception (Form Grabbers)
Instead of relying on network sniffing, form grabbers extract data directly from web forms before it is encrypted and transmitted. This technique is used to capture:
- Login credentials
- Payment form details
- Personally identifiable information (PII)
3. Clipboard Monitoring and Hijacking
Infostealers actively monitor clipboard activity, watching for sensitive content such as:
- Crypto wallet addresses
- Credentials
- Bank account numbers
Some malware can also replace clipboard contents, often swapping crypto addresses with attacker-owned ones to hijack transactions.
4. Remote Access Capabilities (RAT-like Behavior)
Advanced stealers may incorporate Remote Access Trojan features, granting attackers persistent, real-time control over the compromised system. This access enables:
- File browsing and extraction
- Real-time surveillance
- Privilege escalation and lateral movement
Examples: Agent Tesla, LokiBot, TrickBot
5. Screen Capturing
To capture data not easily stored in files or memory, infostealers may periodically take screenshots — especially when users are:
- Logging into sensitive accounts
- Accessing internal tools
- Viewing confidential documents
6. Session Token and Cookie Theft
Some stealers extract session tokens and cookies from browsers, allowing attackers to bypass authentication and hijack active sessions — often without needing passwords or MFA.
Example: Raccoon Stealer
7. File and Document Harvesting
Infostealers crawl the infected system for files that may contain sensitive data, targeting:
- PDFs, Word documents, spreadsheets
- Screenshots and ID scans
- Local email stores and logs
- Password manager exports or .txt password dumps
8. Cryptocurrency Wallet Extraction
Stealers often scan for known crypto wallet software and browser extensions. If private keys or wallet.dat files are found, attackers can steal:
- Bitcoin, Ethereum, and altcoin wallets
- Wallet configurations
- Mnemonic phrases and key backups
Data Distribution
Once data has been exfiltrated from infected systems, threat actors monetize or weaponize it by distributing it across various underground platforms. This typically happens through two main types of cybercrime marketplaces
1. Centralized Marketplaces
Centralized platforms act as organized hubs for buying and selling stolen data. These marketplaces offer searchable interfaces, customer support, reputation systems, and often mimic legitimate e-commerce platforms — but for illicit goods.
A prominent example was Russian Market, which operated as a well-structured marketplace offering “bots” containing stolen credentials, cookies, browser fingerprints, and session tokens. Buyers could browse and purchase entire digital identities, enabling seamless impersonation of victims across multiple platforms.
Decentralized Marketplaces
In contrast, decentralized marketplaces rely on less structured distribution channels such as:
- Telegram groups and channels
- Dark Web forums
- Peer-to-peer trading networks
- Private brokers
The Structure and Value of Stealer Logs
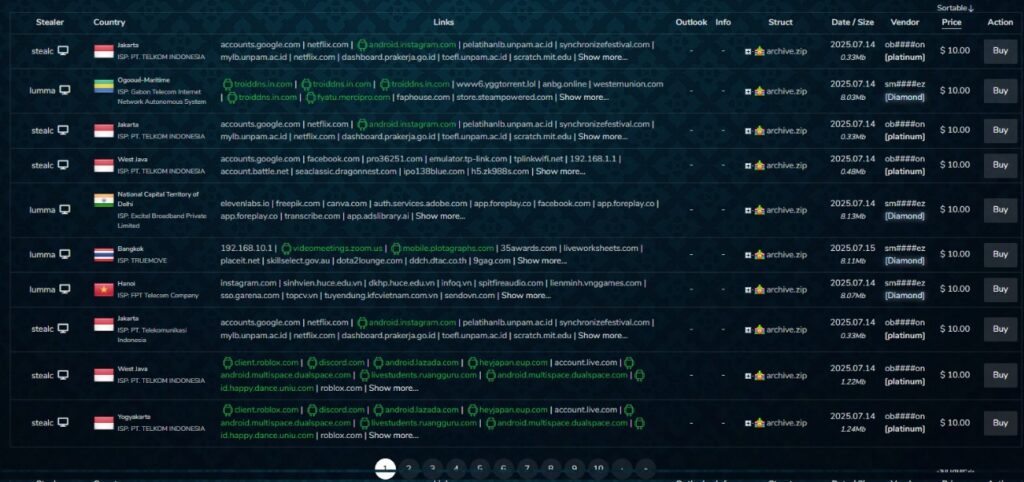
Once exfiltrated, the stolen data is compiled into structured logs that are easy for cybercriminals to navigate, filter, and exploit. These logs are typically formatted in JSON, CSV, or plain text, allowing for seamless parsing and bulk analysis. The objective is to make the data immediately actionable and valuable on underground marketplaces.
Typical Contents of a Stealer Log:
- Credential Sections: Grouped by site or application, often including usernames, email addresses, and passwords
- Cookie and Session Data: Browser cookies and session tokens to enable account hijacking
- Browser History & Autofill Data: Insights into user behavior and potential additional attack vectors
- Application Data: Credentials or tokens for desktop apps like FTP clients, crypto wallets, and messaging platforms
- Metadata: IP address, hostname, operating system details, timezone, and hardware fingerprints for profiling the victim’s environment.
Sample Stealer Log for Illustration
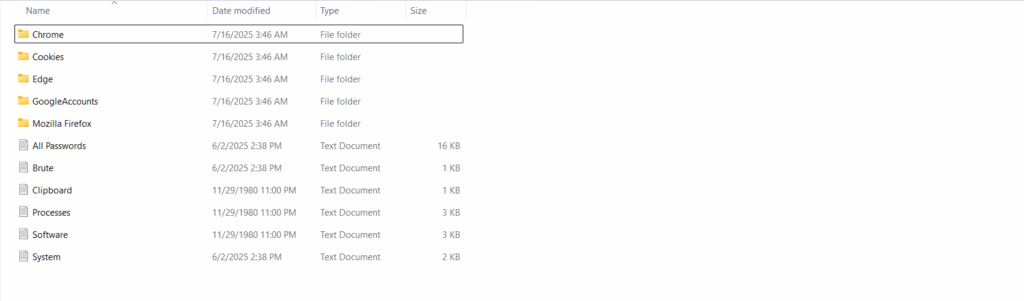
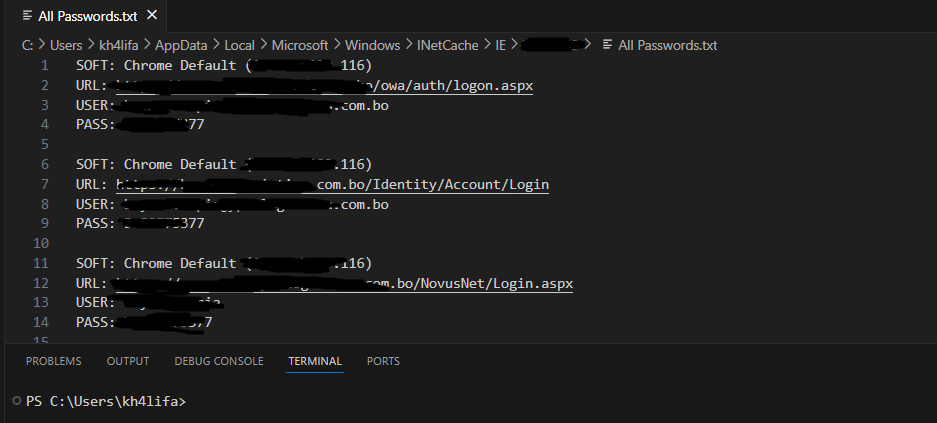
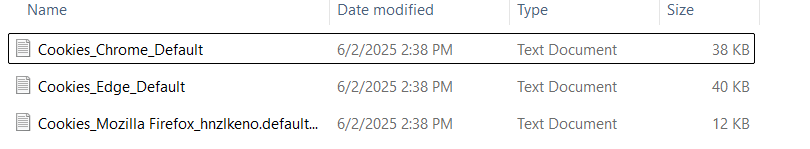
Stealer logs have become one of the most valuable commodities driving modern cybercrime. No longer limited to isolated breaches, today’s credential theft landscape is shaped by the mass collection, resale, and weaponization of sensitive information harvested through infostealer malware.
A striking example of this shift is the ALIEN TXTBASE leak discovered in early 2024. This massive database contained over 23 billion rows of stolen data — including usernames, passwords, browser cookies, session tokens, and personally identifiable information (PII) — aggregated from thousands of infostealer infections. Distributed widely across dark web forums and Telegram channels, TXTBASE illustrates the industrial scale of data theft and its growing role in enabling cybercrime-as-a-service.
How Stealer Logs Are Traded on the Dark Web
In the complex and ever-evolving ecosystem of cybercrime, stealer logs have emerged as one of the most actively traded digital assets. Generated by infostealer malware, these logs contain a goldmine of sensitive data — including login credentials, session cookies, banking information, crypto wallet keys, browser fingerprints, and more.
While some of this data occasionally surfaces in public breaches or leaks, the majority is exchanged quietly across private, underground channels where threat actors buy, sell, or trade access to millions of compromised identities.
Conclusion
Infostealers have become a formidable threat in today’s cyber landscape, capable of silently extracting a wide array of sensitive data from compromised systems — including credentials, financial information, browser artifacts, and crypto assets. Their efficiency, scale, and integration into broader cybercriminal operations make them a cornerstone of modern cybercrime.
Understanding how infostealers operate, how stolen data is distributed, and how it’s ultimately weaponized is essential for building effective defenses. Yet, it’s equally important to acknowledge the limitations and inconsistencies in stealer logs — including false positives, accidental infections, and data integrity issues — which can complicate analysis and response.
By staying vigilant, adopting layered security controls, and leveraging threat intelligence to monitor underground activity, both individuals and organizations can better defend themselves against the evolving infostealer threat landscape.