INTRODUCTION
In the evolving threat landscape, threat actors and ransomware groups continually adapt and refine their methodologies to execute data exfiltration operations for either espionage or extortion purposes.
At Buguard HUMINT Unit “Dark Atlas Squad”, we recently responded to a ransomware incident carried out by Medusa Ransomware Group. Their OPSEC failure allowed us to infiltrate their cloud account for a certain amount of time and access the data they had been exfiltrating over time.
In this case, Medusa Group utilized the infamous exfiltration tool Rclone, which many ransomware groups use to exfiltrate data from the victim to their cloud account.
Rclone supports over 70 cloud providers for data transfer, with services like mega.nz and mega.io being the most frequently used by ransomware groups. Notably, we observed Medusa utilizing put.io to store their exfiltrated data. This was discovered when accessing the configuration file they inadvertently left behind.
OPSEC FAIL
During our investigation, We observed the threat actor dropped rclone.exe to the following location C:\Windows\AppCompat\
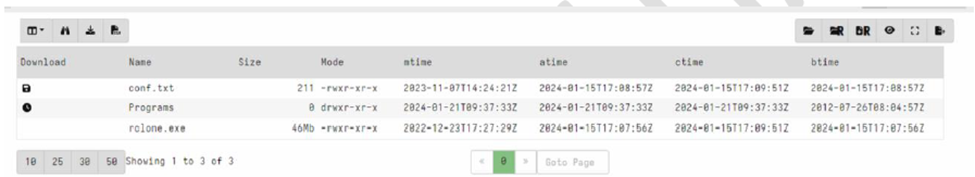
Rclone offers two options for users to set their configuration: either by passing a configuration file or through shell interactive mode. In this case, the former was used.
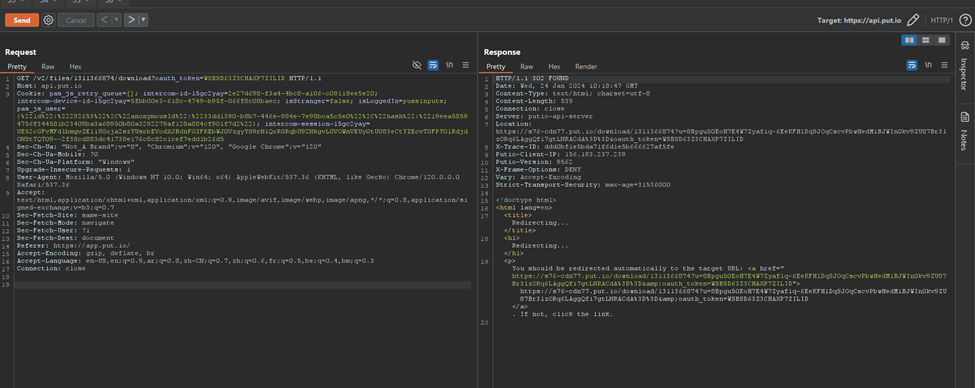
Interestingly, upon inspecting the conf.txt file located in the same directory as Rclone, we observed that the actor utilized the put.io service to exfiltrate data from the DC.
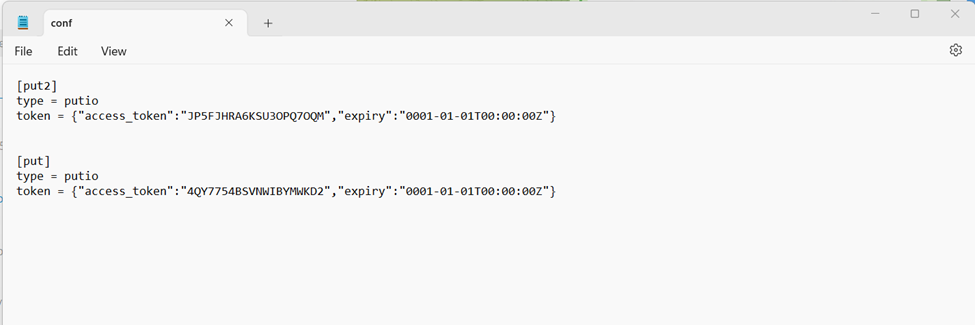
EXPLOITATION AND RECOVERY
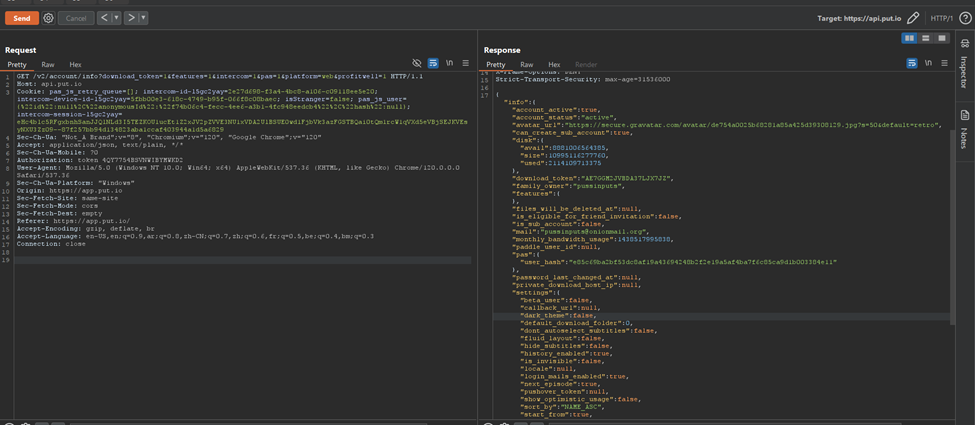
Upon identifying the put.io token, we reviewed the put.io API documentation. We discovered that full authentication required a client_id and client_secret, which we did not have.
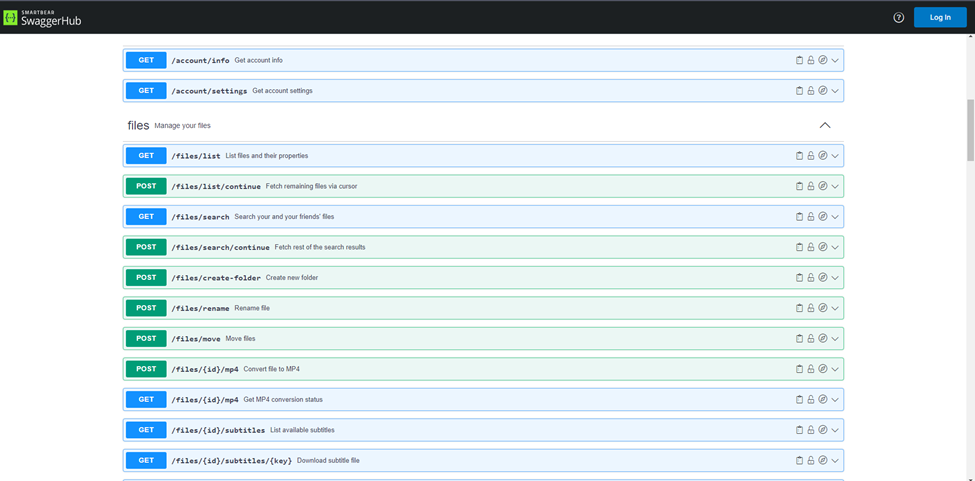
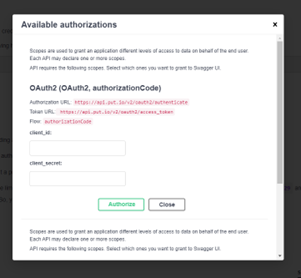
Instead of using the official API, we explored the application as regular users and found that a single token could fully authenticate us. Using Burp Suite, we replaced our token with Medusa’s token, gaining full access to their cloud repositories.
The email associated with their account was “pussinputs@onionmail.org”.
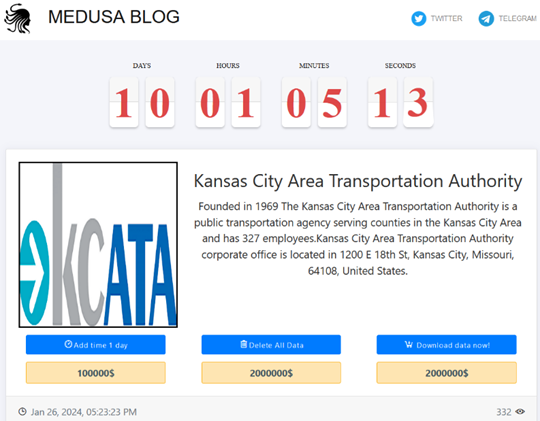
This access allowed us to see all the exfiltrated data from victims, including the Kansas City Area Transportation Authority (KCATA).
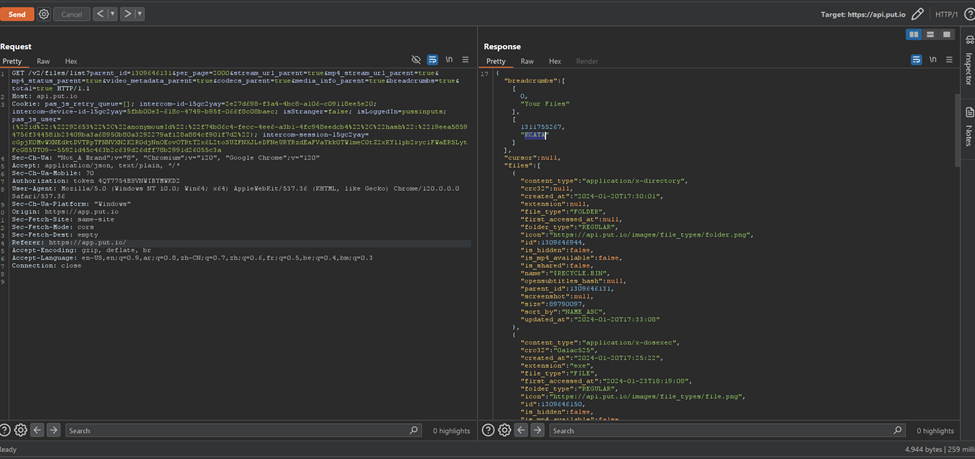
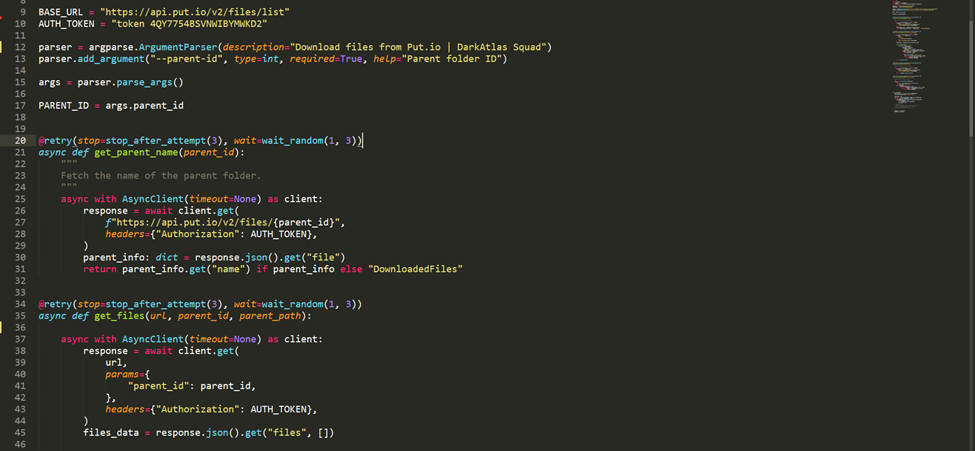
Then, we started re-capturing our customers’ stolen data by creating zips and downloading them.
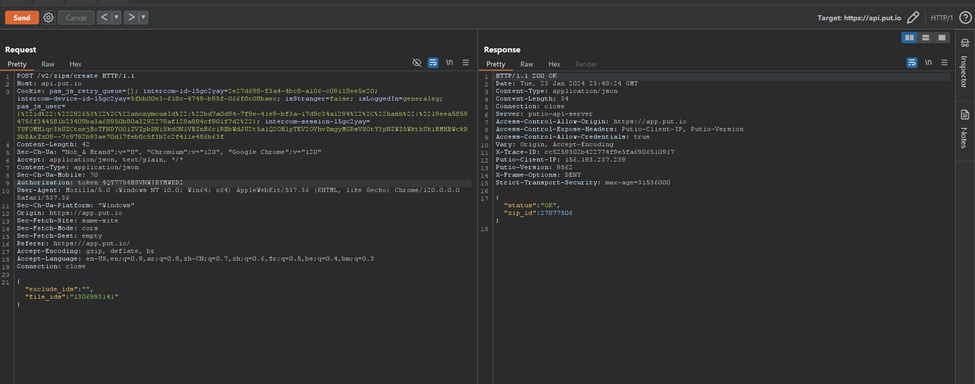
We wanted to do the same for all the affected victims by the Medusa Gang.
We automated this process using a Python script to complete the task swiftly before the attackers noticed.
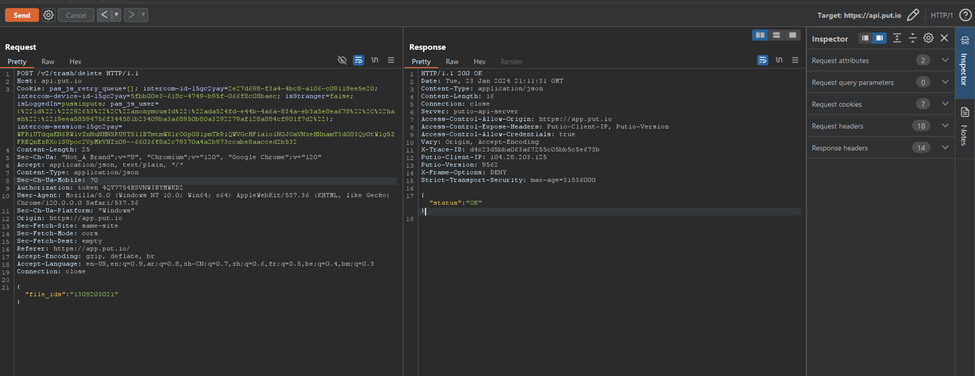
Once we did this, we started to delete some sensitive files belonging to the victims.
We contacted as many victims as possible and helped them to complete the recovery process.
Finally, Dark Atlas Squad crafted a sigma rule to help detect such incidents inside your network.
title: DNS Query To Put.io
id: 37563bef-6951-4912-8516-308b0dffd3c3
status: experimental
description: Detects DNS queries for subdomains related to Put.io sharing website
references:
- Internal Case
author: Omar Khaled (beacon_exe)
date: 2024/02/28
logsource:
product: windows
service: dns-client
definition: 'Requirements: Microsoft-Windows-DNS Client Events/Operational Event Log must be enabled/collected in order to receive the events.'
detection:
selection:
EventID: 3008
QueryName|contains:
- 'api.put.io'
- 'upload.put.io'
- 's111.put.io'
condition: selection
falsepositives:
- Legitimate DNS queries and usage of Put.io
level: mediumThat’s it for today. Thank you for reading! Shout out to our beacon_exe & GeneralEG for this research.
Stay safe, and if you ever face ransomware or a data breach, Email us at Hello@Darkatlas.io!