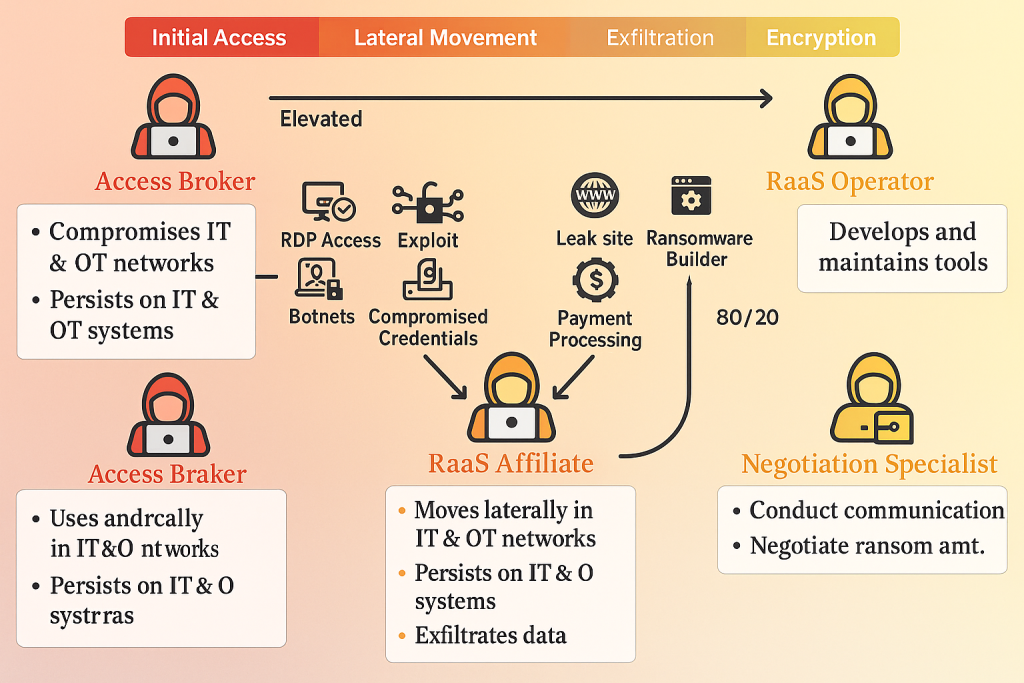
Ransomware isn’t just about locking files—it’s a multi-stage, coordinated intrusion. It’s less like a virus and more like a heist: planned, strategic, and devastating. Threat actors methodically breach networks, escalate privileges, exfiltrate data, and then deploy encryption—all while staying under the radar. I’ve seen companies brought to their knees by these operations. To effectively defend against ransomware, you must understand its lifecycle and the tools adversaries leverage—especially core enterprise technologies like Active Directory, Kerberos, and domain controllers.
With admin access, attackers begin moving through the network — a phase known as lateral movement. They use stolen credentials for techniques like Pass-the-Hash, or leverage trusted tools such as PSExec and WMI to remain inconspicuous. Their primary target is the domain controller; once compromised, they gain control over the entire network. Attacks like Ryuk have shown how quickly threat actors can move laterally using tools like SMB and RDP without triggering alerts.
Next comes data theft and encryption. Before encrypting files, attackers often exfiltrate sensitive information — such as customer data or trade secrets — using tools like Rclone. Then, they deploy the ransomware, encrypting data across the environment. Double extortion is now common: if victims refuse to pay, attackers not only deny access to critical files but also threaten to leak stolen data. Backups are frequently deleted as well, to eliminate recovery options entirely.
it’s also a critical window for defenders to detect and respond. Understanding how adversaries exploit Active Directory, Kerberos, and domain controllers equips you with the insight needed to disrupt their operations before it’s too late.
Initial Access
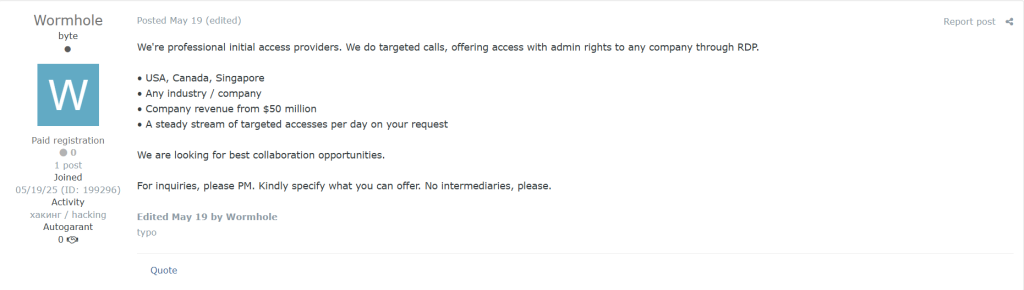
Ransomware attacks typically begin with initial access — the stage where attackers quietly infiltrate a network before launching their full-scale operation. This access is often gained through a combination of technical exploits and human error. A significant aspect of this phase involves pentesters-for-hire — skilled intruders who breach systems and then sell access to ransomware groups. These actors are active on underground forums such as xss.is, exploit.in, BreachForums, and especially RAMP, where network access is traded for as little as $200 to as much as $3,000, depending on the size and value of the target.
Buyers often use platforms like ZoomInfo to assess a company’s annual revenue. If it’s under $5 million, they typically pass — the return isn’t worth the risk. The primary focus is on larger organizations in the U.S. and Europe, where strict data privacy laws like GDPR create additional pressure to pay quickly. If a pentester manages to gain access to a domain controller (DC), the asking price can increase by up to 80%, since DC access provides complete control over the target’s network.
Vulnerability-Based Initial Access
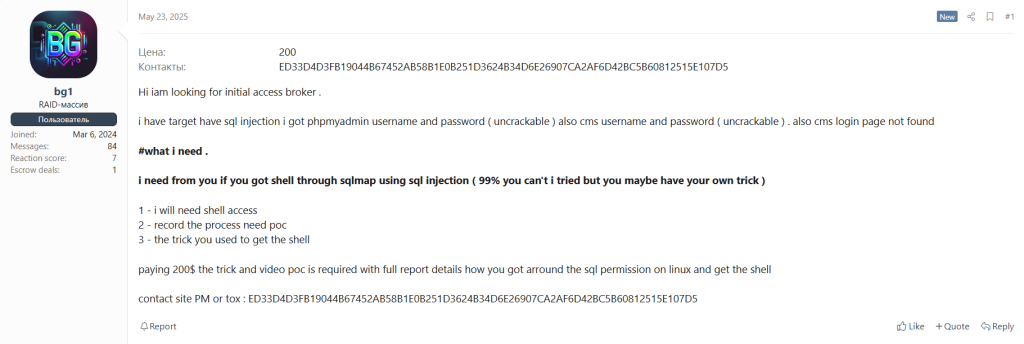
Attackers actively scan for vulnerable internet-facing systems such as RDP, VPN appliances, and enterprise software like Microsoft Exchange. They exploit well-known vulnerabilities — like ProxyLogon or Log4j — to gain unauthorized access. Tools such as Nmap, Nessus, and Metasploit are commonly used to identify and exploit these weaknesses.
If an exposed RDP port is found with a weak password, attackers may brute-force it or use stolen credentials to gain entry. Exploits for these vulnerabilities are frequently traded on underground forums like exploit.in. The more critical the flaw, the higher its market value.
—
SIM Swapping and Social Engineering
Phishing remains one of the most common initial access methods. Attackers craft emails that appear to come from a manager, HR representative, or trusted vendor. These emails typically contain either a malicious attachment — often a Word document with embedded macros — or a link to a fake login page that closely mimics a legitimate one. Opening the document or entering credentials on the spoofed site installs malware such as Emotet, TrickBot, or Qakbot, granting the attacker a foothold in the network. Pentesters often use similar techniques, creating convincing messages designed to trigger urgency, such as fake password reset notices. Many rely on ready-made phishing kits, which are readily available on RAMP, to launch mass campaigns efficiently.
Using Leaked Passwords in Credential Stuffing
Compromised credentials from previous data breaches are a frequent entry point for attackers. They use these stolen usernames and passwords to attempt logins on services such as VPNs, RDP, or Office 365 — a tactic known as credential stuffing. Users who reuse passwords across multiple platforms are particularly at risk. Pentesters often gather these credentials through phishing campaigns or keyloggers and then sell them on forums like BreachForums.
At DarkAtlas Threat Intel Platform, we maintain one of the largest collections of compromised credentials and infostealer logs, providing critical insights that help organizations detect and respond to these threats faster.
Exploiting Third-Party Vendors
Another effective tactic involves targeting companies through their third-party vendors. These supply chain attacks are more complex to execute but can cause widespread damage. For example, the SolarWinds breach saw attackers implant malware in a software update, compromising thousands of organizations. Similarly, the Kaseya incident resulted in ransomware being deployed to numerous clients via a managed service provider. Pentesters frequently focus on smaller vendors with weaker security controls, especially those connected to larger enterprises. Access gained through these vendors can fetch between $2,000 and $3,000 on forums like RAMP or xss[.]is, making it a high-risk, high-reward strategy.
Exploit Kits and Malvertising Campaigns
Sometimes, attackers compromise legitimate websites or run malicious ads that silently install malware the moment a user visits the page. These drive-by downloads often exploit outdated browser plugins like Flash or Java and are delivered through exploit kits such as Rig or Neutrino. Pentesters set up these traps and sell the resulting network access on forums like BreachForums, typically for $300 to $800, depending on the size and value of the infected network. These attacks are stealthy, fast, and easily scalable.
Internal Compromise
Sometimes, the breach comes from within. Disgruntled employees or contractors may sell access to ransomware groups—ranging from VPN credentials and admin passwords to full domain controller logins. Pentesters actively recruit insiders through forums like RAMP or xss.is, often offering over $8,000 for direct access. While less common, insider threats are especially dangerous because they can bypass most security controls, making detection and response far more difficult.
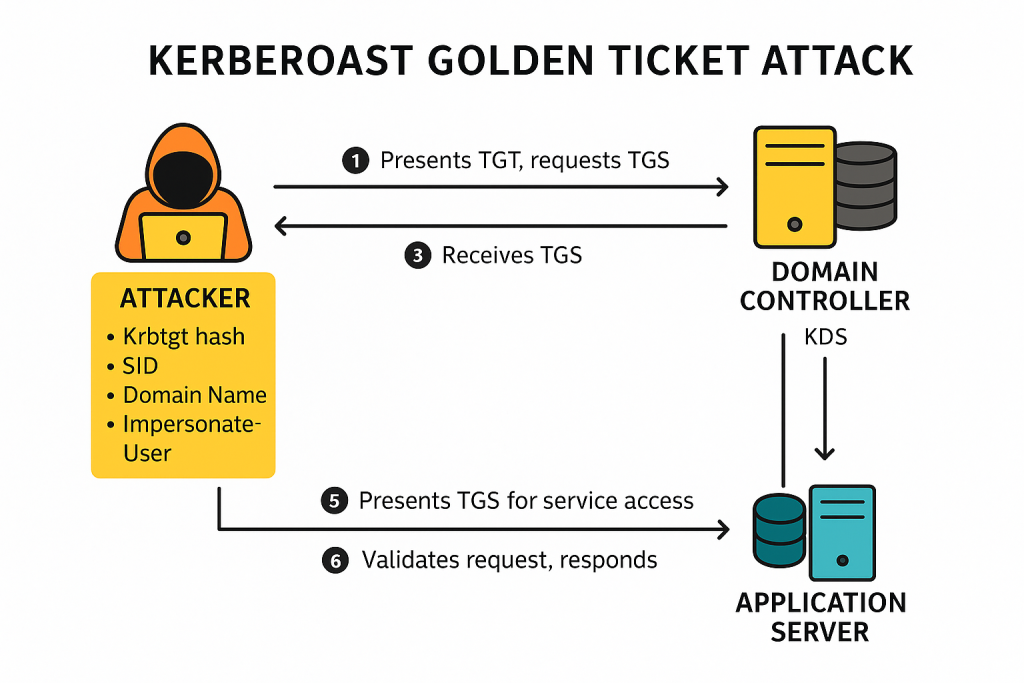
Privilege Escalation
Once ransomware attackers finish mapping the network during reconnaissance, the next step is privilege escalation—climbing from a low-level account to one with elevated permissions, such as domain admin. In Windows environments, Active Directory (AD) becomes the primary battleground, with Kerberos, the authentication protocol, as a key target. This stage is where attackers leverage techniques like Kerberoasting, token impersonation, and credential dumping to gain full control. This section outlines how they exploit Kerberos and other vulnerabilities to escalate privileges and dominate the network using a wide range of tools and tactics.
Final Stage: Data Exfiltration and Encryption
Ransomware operators reserve their most destructive actions for the final stage—data exfiltration and encryption. Exfiltration involves stealing sensitive data such as customer information, financial records, and proprietary source code. This enables double-extortion tactics, where victims are pressured to pay not only to regain access but also to prevent public data leaks. Encryption renders systems unusable, making recovery impossible without a decryption key. This section provides a technical breakdown of how attackers exfiltrate and encrypt data using tools like StealBit, Exmatter, Rclone, and peer-to-peer methods such as Tox, along with techniques like semi-encryption and ZIP header corruption. Real-world incidents, including Colonial Pipeline and JBS Foods, illustrate these tactics in action.
Targeted Data Exfiltration
Data exfiltration is all about stealing high-value files and transferring them to attacker-controlled servers. It’s a crucial step in double-extortion attacks. Threat actors prioritize sensitive files such as databases, intellectual property, and financial documents. They employ both custom-built tools and open-source utilities to automate this process, ensuring stealth and speed.
StealBit (Used by LockBit)
StealBit is a purpose-built tool designed for speed and simplicity. Used by LockBit affiliates, it scans victim systems to identify high-value files based on extensions (e.g., .docx, .pdf, .sql) or directories (e.g., C:\Data). It compresses files to reduce bandwidth use and transfers them via HTTP or FTP. In many cases, StealBit operates automatically, copying files to a staging folder before upload. designed for rapid exfiltration ahead of ransomware deployment, as seen in the Accenture breach.
Exmatter (Used by BlackMatter and Conti)
Exmatter, developed in .NET, targets file types like source code, CAD designs, and .rdp shortcuts. It scans all drives but avoids system folders to focus on operational data. The tool uploads prioritized files via SFTP or WebDAV. According to Kroll, Exmatter played a key role in Conti operations, rapidly stealing engineering and proprietary data to increase ransom pressure.
Rclone: Leveraging Cloud Storage
Rclone is an open-source tool favored by ransomware groups for its ability to blend in with legitimate network activity. It synchronizes local files with cloud services like Mega, Google Drive, or Dropbox. Rclone encrypts files and supports chunking for stealthy transfers. Used in multiple LockBit and BlackByte attacks, Rclone was highlighted by CISA for its role in exfiltrating data from healthcare targets in 2022.
Peer-to-Peer (P2P) Data Transfers
Advanced attackers use P2P methods like the Tox protocol, an encrypted, decentralized communication platform with no central server. This makes monitoring and blocking difficult. In one 2020 Maze attack, Tox was scripted to transmit stolen databases in segments, ensuring completion while maintaining anonymity.
Another method involves torrenting. Groups like REvil create .torrent files of stolen data and seed them via clients like qBittorrent. The 2021 JBS Foods attack saw REvil exfiltrate financial records through torrents, masking their destination using BitTorrent’s distributed design.
Attackers often compress files with WinRAR or 7-Zip, stage them in C:\Temp, and track file interactions via the Master File Table (MFT) for stealth and efficiency. Conti was observed using MFT parsing to prioritize high-value files in 2024.
System Lockdown: Encryption Techniques
Once data is stolen, attackers deploy encryption to paralyze operations and maximize leverage.
Hybrid Encryption
Most ransomware, including LockBit 3.0, uses a hybrid approach:
- ChaCha20 (symmetric) encrypts file content.
- RSA-2048 (asymmetric) encrypts the ChaCha20 key.
Each file gets a unique ChaCha20 key, and its RSA-encrypted counterpart is stored in ransom notes (e.g., .README.txt). This method was confirmed in the REvil-JBS attack, where meatpacking systems were encrypted.
Semi-Encryption
To accelerate operations, attackers often partially encrypt files. LockBit 3.0, for example, encrypts the first 5 bytes every 5,000 bytes in large files (>1MB), corrupting them just enough to render them useless.
ZIP Header Corruption
Attackers target metadata within ZIP archives, encrypting only the central directory structure. Without this, archives become unrecoverable—even if their contents remain intact. This method was employed by LockBit 2.0 in a 2021 attack on a U.S. manufacturer
Sparse File Encryption
For large files like SQL databases, attackers use sparse encryption, targeting only strategic segments. DarkSide employed this technique in the 2021 Colonial Pipeline attack, encrypting over 100GB with minimal processing time.
Backup Destruction
To block recovery, attackers delete Volume Shadow Copies using built-in Windows tools like vssadmin and wmic. LockBit 3.0 was seen doing this in a 2023 healthcare incident, per CISA.
GPO Deployment via Domain Controllers
Attackers with domain admin rights use Group Policy Objects (GPOs) to deploy ransomware across entire networks. This technique was central to Conti’s 2021 campaign.
Conclusion
Data exfiltration and encryption represent the final—and often most devastating—phases of a ransomware attack. By this stage, the adversary has already infiltrated the environment, escalated privileges, and mapped out critical assets. The tactics detailed above demonstrate that modern ransomware groups are not only financially motivated but technically sophisticated, employing a blend of custom-built malware, open-source utilities, and stealthy transfer protocols to maximize pressure on victims.