Ransomware is no longer just a malicious program deployed by a single attacker — it has evolved into a complex, profit-driven ecosystem operating much like a legitimate business model. Today’s ransomware operations involve multiple specialized actors, automated platforms, and underground services working together to maximize impact and financial gain.
From Initial Access Brokers selling compromised network access, to affiliates executing attacks through Ransomware-as-a-Service (RaaS) platforms, and leak sites used to pressure victims through public exposure, each component plays a critical role in the attack lifecycle. This distributed model has lowered the barrier to entry for cybercriminals while significantly increasing the scale and sophistication of ransomware campaigns.
In this article, we will break down the ransomware ecosystem, explain the key roles and tools involved, and show how these components connect, so defenders can identify where to detect and disrupt attacks earlier.
What Is a Ransomware Ecosystem?
A ransomware ecosystem is the network of people, services, and infrastructure that supports an attack—from initial entry into a network to extortion and payment collection. It includes:
- Access providers who sell compromised entry points
- Affiliates who deploy ransomware and negotiate payments
- Operators who run the RaaS platform, tooling, and support
- Leak sites used to pressure victims through exposure
- Supporting services that enable stealth, persistence, and monetization
This model is why ransomware is now more scalable and resilient than traditional malware operations.
Key Roles and Concepts in the Ransomware Supply Chain
Below are the most common ransomware roles and terms you’ll see in modern campaigns:
| Term | Definition |
|---|---|
| Affiliate | An attacker who leases or utilizes a Ransomware-as-a-Service RaaS platform to conduct attacks, typically sharing a percentage of the ransom payment with the operator. |
| Initial Access Broker (IAB) | A cybercriminal who sells access to compromised networks (VPN, RDP, credentials, web shells) to ransomware groups and affiliates. |
| Double Extortion | A ransomware tactic involving both data A tactic combining data encryption + data theft. Victims are pressured to pay for recovery and to prevent public exposure. |
| Dedicated Leak Site (DLS) | A publicly accessible platform, usually hosted on the dark web, where ransomware groups publish stolen data to increase pressure during ransom negotiations. |
| Builder | A tool provided by RaaS operators that enables affiliates to generate customized ransomware payloads based on selected configurations. |
| Panel / Dashboard | A web-based management interface used by affiliates to track victims, generate payloads, monitor infections, and manage communications. |
| Cryptor | A software utility designed to obfuscate malicious code in order to bypass security detection mechanisms. |
| Locker | A ransomware variant that restricts user access to systems or devices instead of encrypting files. |
| Stealer Logs | Data stolen by info stealer malware (credentials, tokens, cookies). Often used for lateral movement or sold to IABs. |
How Ransomware Evolved: A Short History
Ransomware has existed for decades, but its growth accelerated dramatically after 2013 as criminal groups adopted scalable business models.
AIDS Trojan (1989)
Created by Joseph Popp, the AIDS Trojan is widely recognized as the first documented ransomware case, demanding payment to restore access.
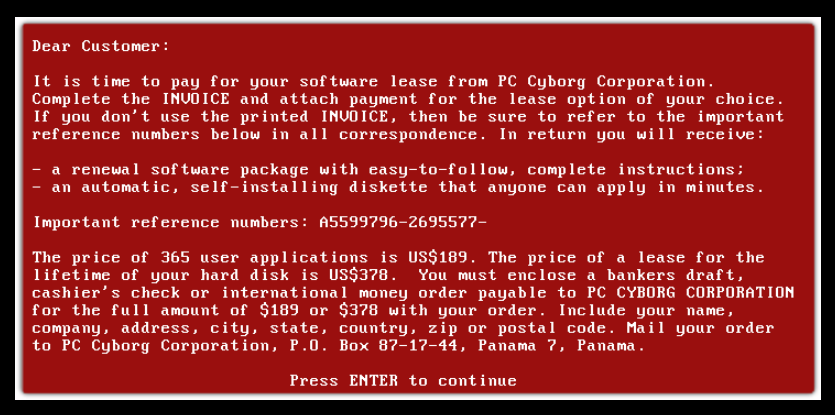
GPCode / PGPCoder
Early ransomware families that encrypted files and demanded ransom—introducing what later became common cryptovirology behavior.
Modern Expansion (2013–Present)
Since 2013, ransomware operations have experienced rapid growth, evolving from small-scale, opportunistic attacks into highly organized cybercriminal enterprises. Over the years, threat actors have adopted more advanced techniques, monetization strategies, and automation tools, allowing ransomware groups to scale their operations, target larger organizations, and generate millions of dollars in illicit revenue worldwide.
Major Ransomware Campaigns That Shaped the Ecosystem
These examples show how ransomware matured, especially through RaaS, automation, and double extortion.
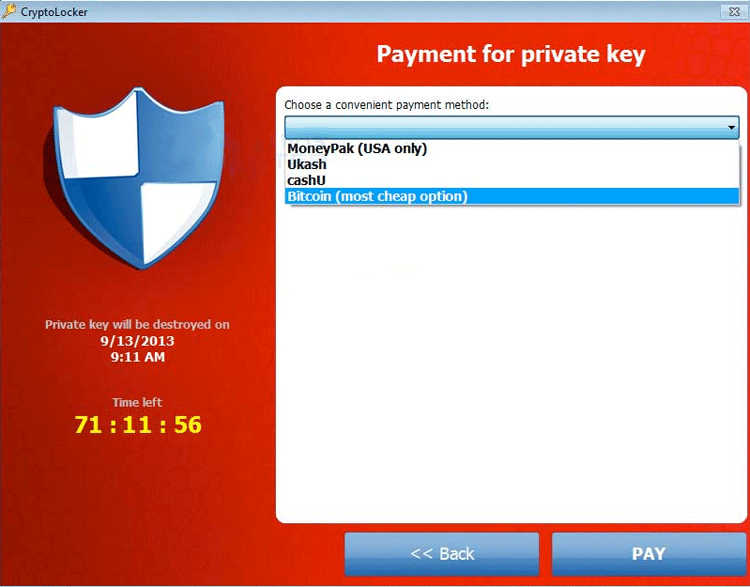
1- CryptoLocker (2013–2014)
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late May 2014. The attack utilized a trojan that targeted computers running on Microsoft Windows, and was believed to have first been posted to the Internet on 5 September 2013. It propagated via infected email attachments, and via an existing Gameover ZeuS botnet. When activated, the malware encrypted certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware’s control servers.
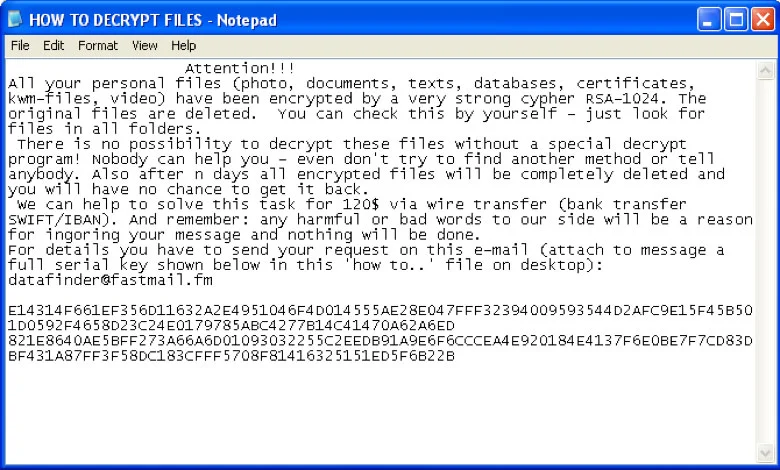
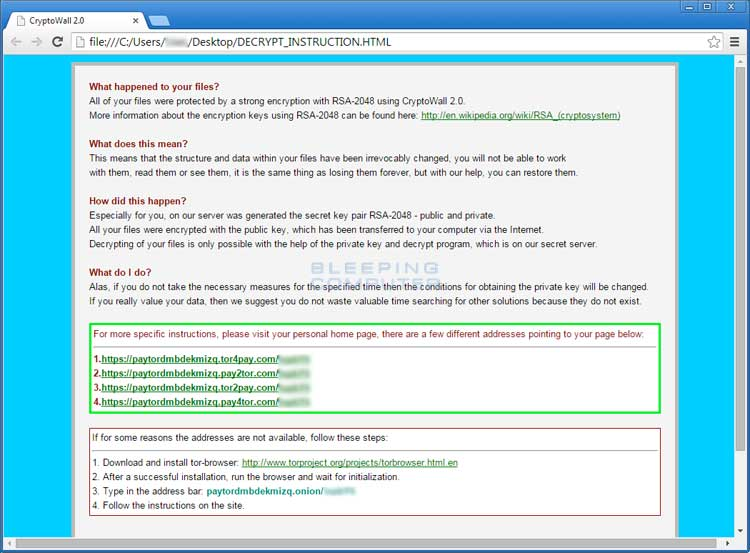
2- CryptoWall (2014)
CryptoWall is a ransomware malware that works by encrypting files on an infected computer and requires users to pay ransom to receive a decryption key. It was initially released in 2014, but it’s been through several iterations, making it a much stealthier version of ransomware than others like it.
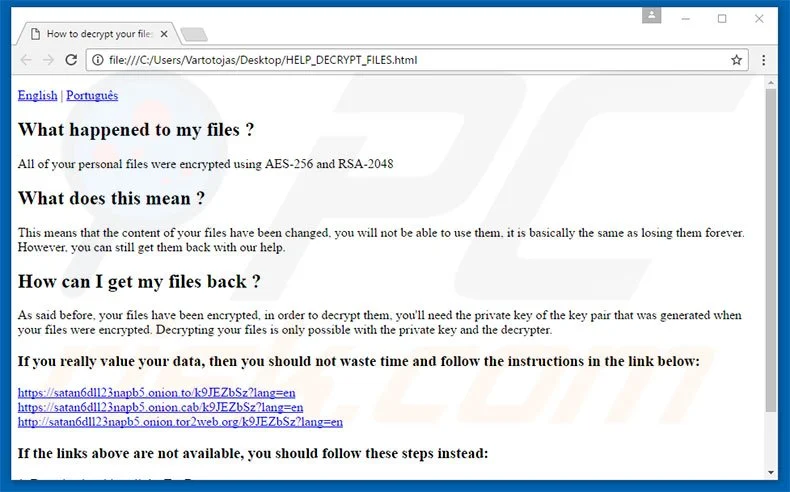
3-Satan
The Satan RaaS platform is a modern approach to ransomware deployment, allowing cybercriminals to easily access and customize ransomware without needing coding skills.
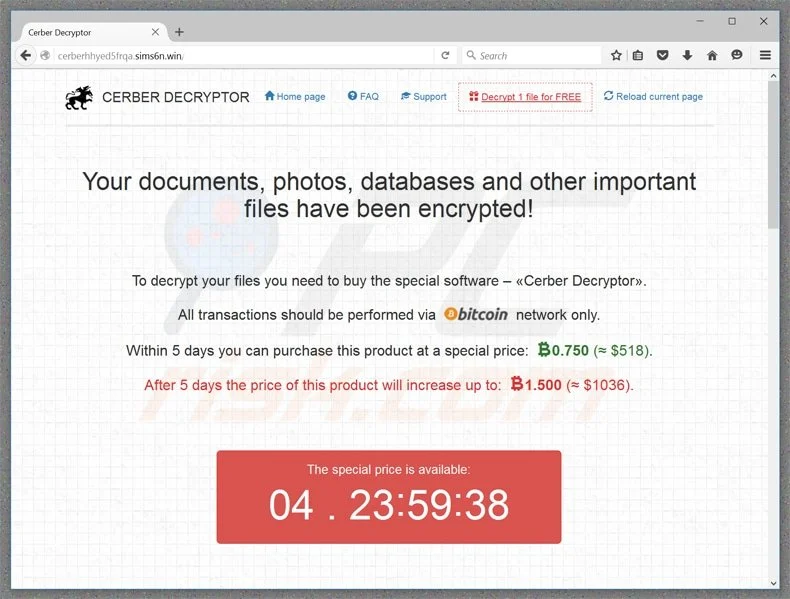
4- Cerber (RaaS)
Cerber ransomware is a type of malware (malicious software) that encrypts your files and then holds them hostage, demanding a ransom payment in exchange for returning them to you. But what makes Cerber different from some other types of ransomware? It comes down to Cerber’s business model: Cerber is ransomware-as-a-service (RaaS).
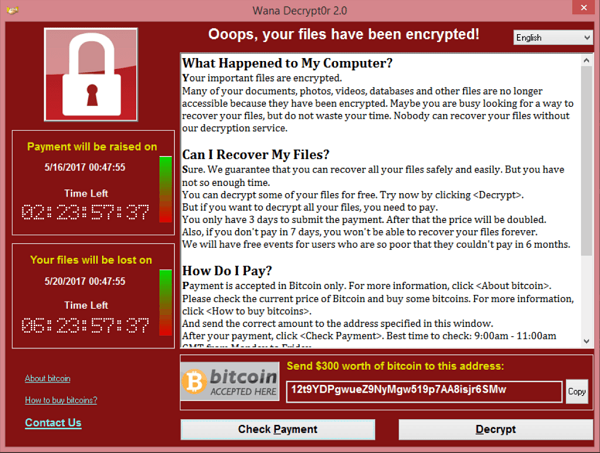
5- WannaCry (2017)
The WannaCry ransomware attack was a worldwide cyberattack in May 2017 by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the form of bitcoin cryptocurrency. It was propagated using EternalBlue, an exploit developed by the United States National Security Agency (NSA) for Microsoft Windows systems. EternalBlue was stolen and leaked by a group called The Shadow Brokers (TSB) a month prior to the attack.
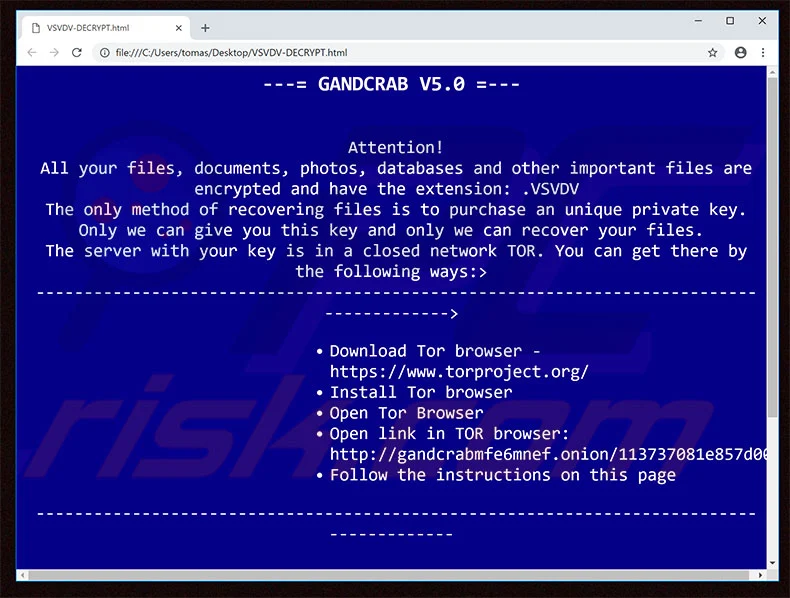
6- GandCrab (2018)
GandCrab is a ransomware-as-a-service variant that was discovered in early 2018. Described as agile ransomware, the actors behind this strain started by publishing the least well-built malware that could possibly work, and improved it as they went along. Advertised in the Russian hacking community on the dark web, this strain is operated in an affiliates program, with those joining the program paying 30%-40% of their earned ransom revenues to the GandCrab author. In return, affiliates get a full-featured web panel and technical support.
7-Sodinokibi / REvil (2019)
Sodinokibi, also known as REvil, is a highly sophisticated ransomware-as-a-service (RaaS) operation that has been active since 2019, known for its double extortion tactics and targeting enterprises globally.
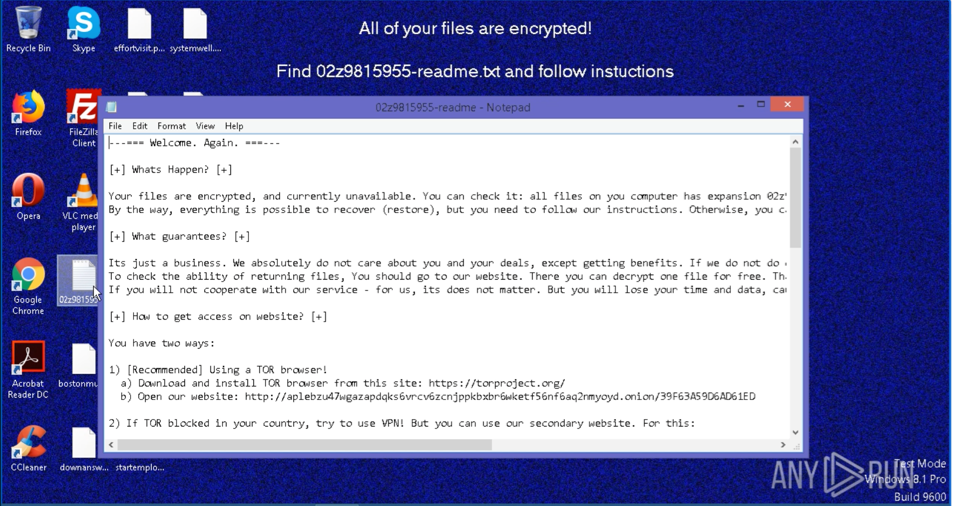
8- Maze (2019)
Since its discovery in 2019, Maze ransomware has consistently made headlines due to its infamous attacks on MSPs and its ability move laterally to other networks. Although this particular strain of ransomware has been used to attack businesses and governmental organizations, its attacks on MSPs are worrying since a single compromise can create a cascade effect on the MSP’s clients, their business partners, and so on.
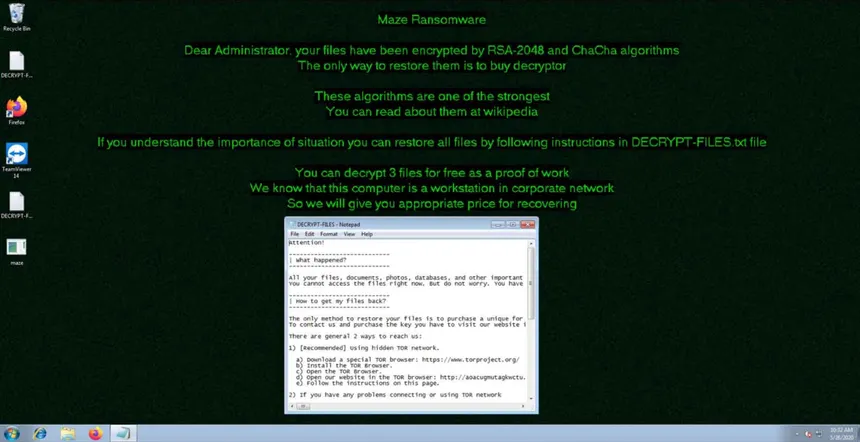
9- Conti (2019–2022)
Conti is malware developed and first used by the Russia-based hacking group “Wizard Spider” in December, 2019. It has since become a full-fledged ransomware-as-a-service (RaaS) operation used by numerous threat actor groups to conduct ransomware attacks.
check out blog about conti.
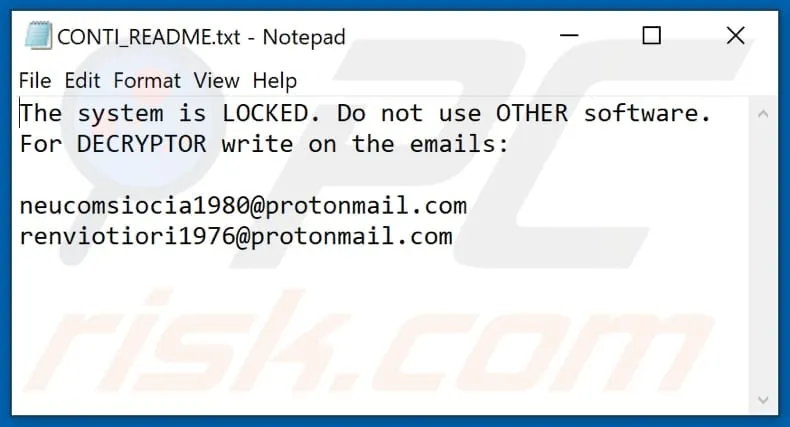
10-LockBit (2022)
LockBit Ransomware-as-a-Service (RaaS) offering with similarities to BlackMatter and BlackCat ransomware. LockBit 3.0 has been in use since at least June 2022 and features enhanced defense evasion and exfiltration tactics, robust encryption methods for Windows and VMware ESXi systems, and a more refined RaaS structure over its predecessors such as LockBit 2.0.

11-BlackCat / ALPHV (2021)
BlackCat, also known as ALPHV and Noberus, is a computer ransomware family written in Rust. It made its first appearance in November 2021. By extension, it is also the name of the threat actor(s) who exploited it.
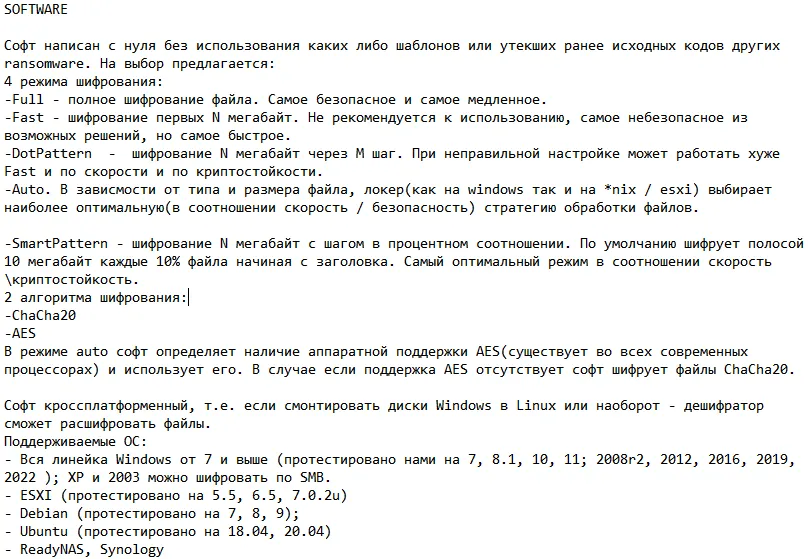
12 – VECT / AETHERION Ransomware (2026)
A newly emerged ransomware-as-a-Service (RaaS) platform first detected in early January 2026, operating with high technical sophistication and a focus on multi-platform attacks.
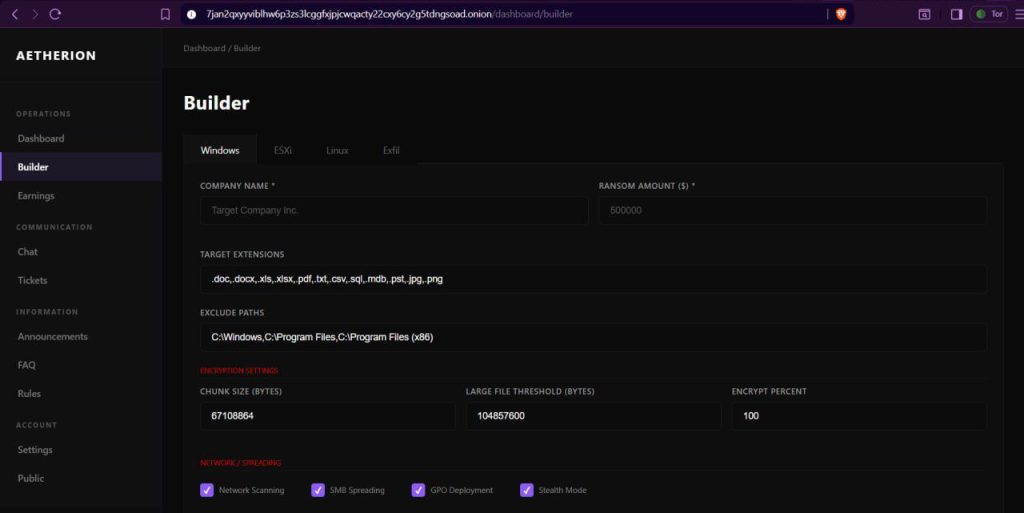
The Initial Access Marketplace: Where Ransomware Often Starts
Many ransomware operations begin before ransomware is even deployed. Access is commonly purchased from an underground market that sells:
- Stolen credentials (from stealer logs)
- RDP/VPN access
- Web shells
- Exposed admin panels and misconfigurations
Key marketplace components include:
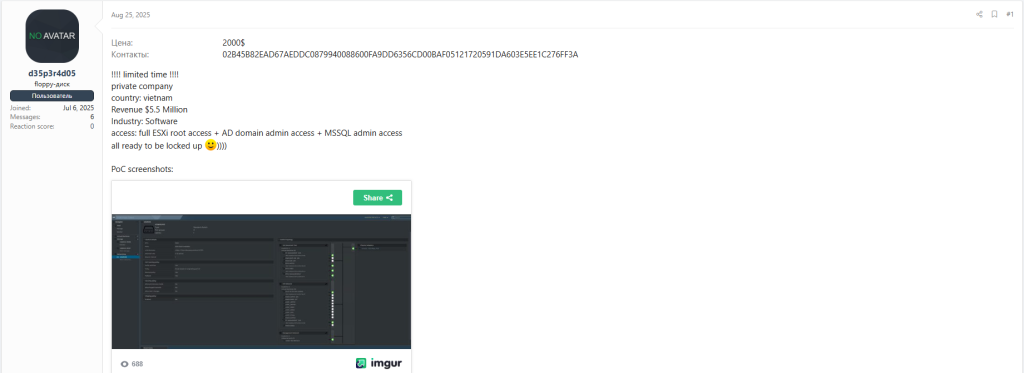
Stealer Logs brokers & Developers
They harvest credentials/tokens and sell them to IABs or directly to affiliates, enabling quick entry and lateral movement.
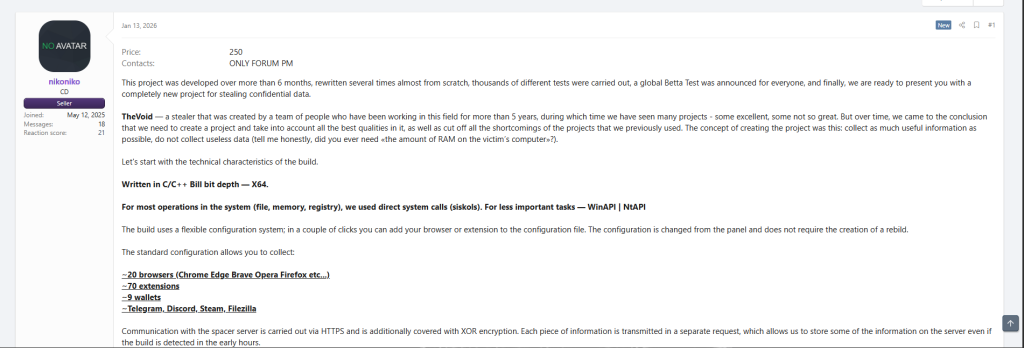
Cryptor
Used to help payloads evade detection during delivery and execution.
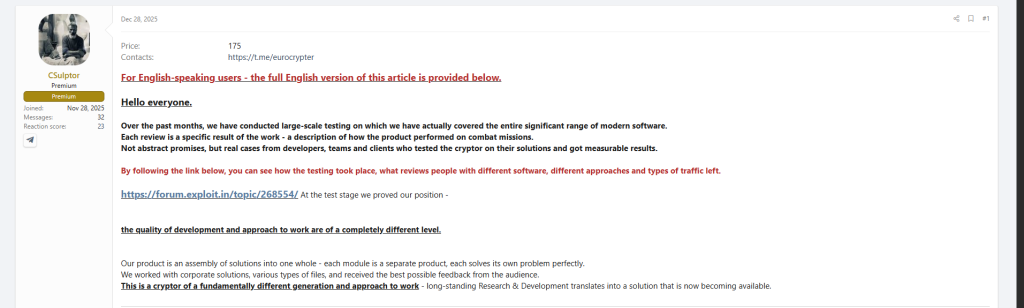
Locker Deployment
The final stage: ransomware payload execution, encryption or lockout, and extortion operations.
Conclusion: Why Understanding the Ecosystem Matters
The ransomware ecosystem has evolved into a mature, highly organized cybercriminal economy, driven by specialization, collaboration, and financial incentives. What began as isolated malware campaigns has transformed into a service-based model where Initial Access Brokers, affiliates, developers, and data leak operators each play a distinct role in executing large-scale attacks.
This ecosystem approach has lowered the barrier to entry for attackers while increasing the speed, reach, and impact of ransomware operations. Techniques such as double extortion, automated tooling, and Ransomware-as-a-Service platforms continue to enable threat actors to adapt rapidly and remain resilient against takedown efforts.
For defenders, understanding the structure and workflows of the ransomware ecosystem is critical. By identifying how access is gained, how payloads are deployed, and how extortion pressure is applied, organizations can better prioritize detection, prevention, and disruption strategies. Ultimately, effective defense requires not only technical controls but also intelligence-driven monitoring and proactive security postures aimed at breaking the ransomware business model itself.